-

Understanding and Countering Stalkers
On May 11, singer Billie Eilish obtained a restraining order against a fan who had repeatedly approached her residence, TMZ…
-

Postmodernism and the Insider Threat
Insider threats are nothing new; factors such as greed, grievance, duplicity, and malice have long served to motivate workers to…
-

Preparing for the Next Crisis
The COVID-19 crisis is unlike anything most of us have experienced in our professional lives. It is presenting an array…
-
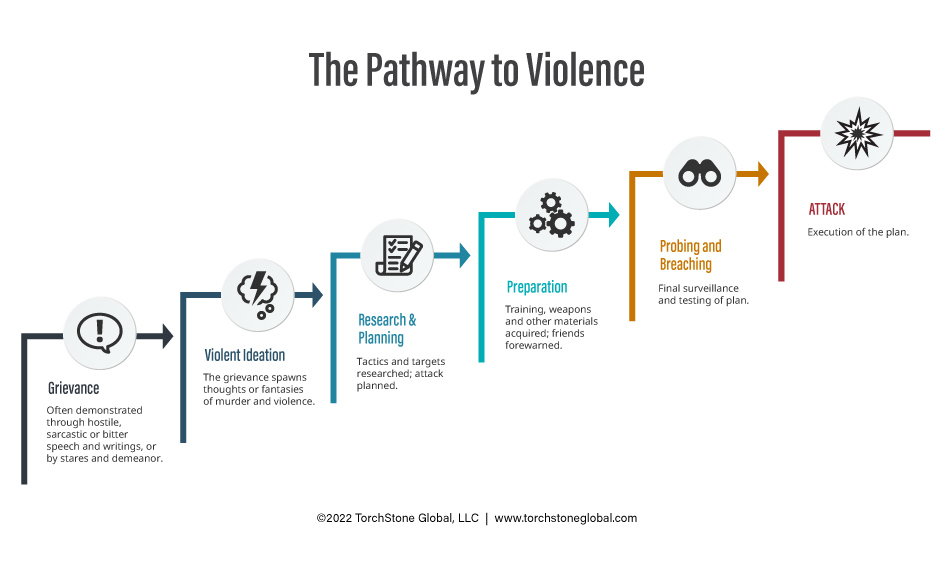
Where the Attack Cycle Intersects the Pathway to Violence
I’ve written about how the concept of the attack cycle is a useful framework protective intelligence practitioners can use to…
-
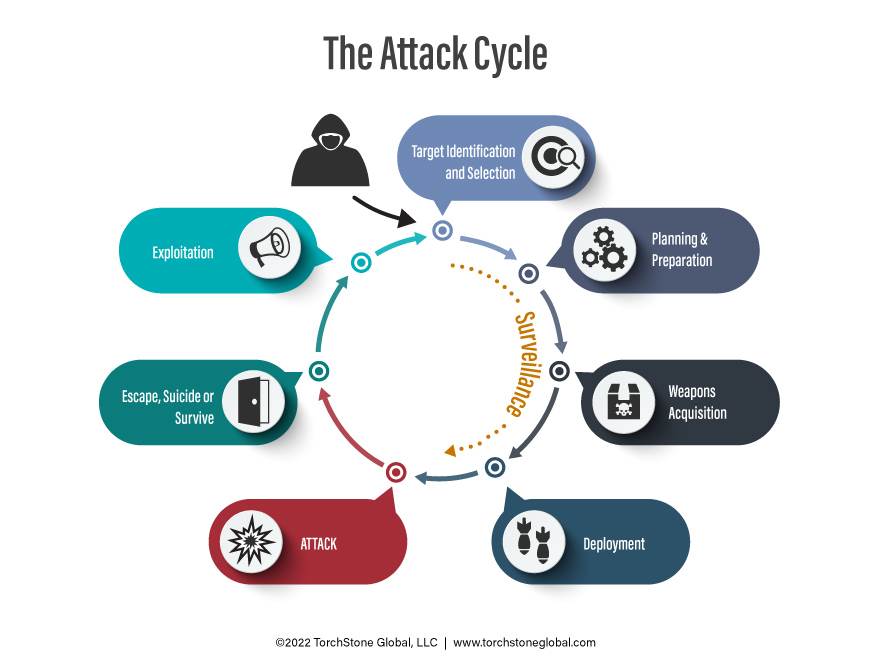
Exploiting Vulnerabilities in the Attack Cycle
In the piece TorchStone Global previously published on understanding the attack cycle, I noted that the most important reason for…
-

International Burn Down a 5G Tower Day
What is Happening: A group of internet activists have declared May 3, 2020 to be “International Burn Down a 5G…
-

The Importance of Understanding the Attack Cycle
In the piece I wrote on the need for, and functions of protective intelligence programs, I discussed how one of…
-

Why Your Company Needs a Protective Intelligence Program
Many people perceive protective intelligence (PI) as some sort of highly-secret government program that is only used to protect the…
CALL US: (877) 897-6428
